FortiSIEM 7.5 Powers the Modern SOC with Agentic AI and Data Sovereignty Compliance
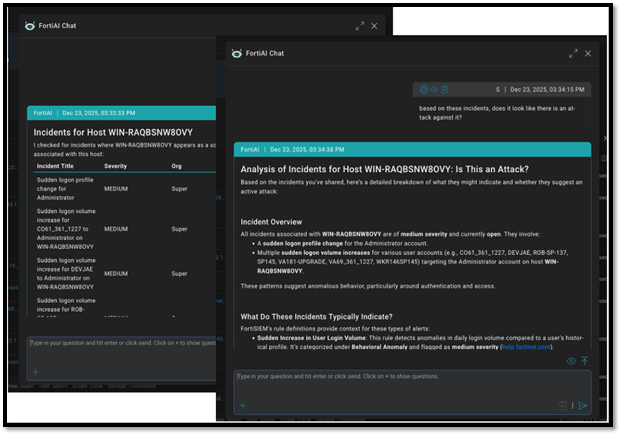
Security Operations Centers (SOCs) are facing a growing challenge as cyber attackers leverage AI to launch faster and more advanced threats. At the same time, concerns around data and operational sovereignty often prevent multinational organizations from running a fully centralized SOC. Addressing these challenges, the newest FortiSIEM release delivers enhanced threat detection capabilities, agentic AI–driven […]
Google Makes Shocking Revelation On Ransomeware

A Google research has shown that “Cyber-thieves have made more than $25m (£19m) from ransomware in the last 24 months. The search engine giant worked on a lot of virtual victims of ransomware to reveal the payment network that works with the malware software. An interview with Black Hat said. “Few of the cash was […]
ICC Awarded ISO 9001:2015

We have been awarded ISO 9001:2015 Quality Certiication for IT Consulting work we do
Nationwide IT Support
iCompuCARE specializes in delivering the highest level of IT support services to our business clients with multiple location support available nationwide. For businesses with multiple locations: Many IT Managers struggle and waste valuable time and resources trying to coordinate so many locations and locating competent service providers. Even more importantly it can be difficult trying […]
Secure Remote File Access – MyWorkDrive

Why MyWorkDrive MyWorkDrive gives your enterprise secure file share access without VPN using your Windows File Shares & Active Directory infrastructure. Remotely edit and share files simply and securely. No Vendor lock-in, No syncing or migrating to a cloud needed.
iCompuCARE appointed as a reseller for FolderIT
iCompuCARE is the Authorized reseller partner of Folderit DMS in Malaysia. Click here for more information
iCompuCARE New Bigger and Better Home
[et_pb_section bb_built=”1″ admin_label=”section”][et_pb_row admin_label=”row” background_position=”top_left” background_repeat=”repeat” background_size=”initial”][et_pb_column type=”4_4″][et_pb_text background_position=”top_left” background_repeat=”repeat” background_size=”initial” _builder_version=”3.0.62″] [/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]
Protect your networks and devices from cyberattacks

More cyberattacks are expected in 2018 and good cybersecurity practices are more relevant now than ever. RANSOMWARE attacks will evolve and hit harder in the upcoming years, says Pikom Cybersecurity chair Alex Liew.Speaking at the Star Empowerment: Cyber Defence & Network Security forum in Petaling Jaya recently, Liew said that most security experts agree that […]
ICompuCare now certified in 3CX

we have passed the 3CX Engineer certification and now we are skilled to configure and deploy 3CX in the cloud. congratulations to our 3CX support
Google launches its own built-in adblocker for Chrome browser

Google has a new strategy to combat pesky pop-up ads that plague internet browser users around the globe. In what appears to be a contradictory move for a company whose profits come largely from advertising, Google is now blocking particularly annoying advertising on its browser, Chrome. The move comes after some 615 million instances of […]
Hackers infect thousands of websites to mine cryptocurrencies

The attack is the first major incident made public in which a new breed of hackers took over a large numbers of websites to effectively create currencies like bitcoin which are generated by using computing power. The attacks made public over the weekend by British security researcher Scott Helme showed more than 4,000 website were […]
Does screen time steal happiness from teens?

Teens who report more time spent on recreational Internet use also report less happiness, self-esteem, and satisfaction with their lives, according to a study published – of all places – online recently in the journal Emotion. The authors of the study analysed data from the Monitoring the Future survey, which has asked thousands of eighth, tenth, […]
To be safe, deactivate debugging mode on Android smartphones

The Android system’s debugging mode can be activated when your device is connected to a computer via USB cable. But even if you enjoy tinkering with your phone’s features, this mode can be a risk when left on. Users are therefore best advised turning it off after use. The main function of the mode, also […]
This browser security extension is reading your social media data

The Chrome extension Browse Secure may sound like it wants to do nothing but make your browser more secure. And yet this extension is collecting contact data from Facebook and LinkedIn once the user is logged in, Germany’s Federal Office for Information Security has discovered. The extension has already been removed from the Chrome Web […]
Don’t use Bluetooth before installing latest security updates.

A Bluetooth connection can leave computers, smartphones and other devices vulnerable to security breaches, so users should quickly install any updates – or turn the function off. That’s the advice of the German Federal Office for Information Security (BSI) in response to the recent “Blueborne” Bluetooth vulnerability, which is thought to have put 8 billion […]
M’sia sees biggest mobile data breach

The personal details of some 46.2 million mobile number subscribers in Malaysia are at stake in what is believed to be one of the largest data breaches ever seen in the country. From home addresses and MyKad numbers to SIM card information, the private details of almost the entire population may have fallen into the […]
Bad Rabbit: A new Petya-like ransomware that’s spreading, but beatable

A new form of ransomware, dubbed Bad Rabbit, is infecting computers via drive-by attacks masquerading as Flash updates.This latest form of rapidly spreading ransomware is believed to be a variant of the Petya family; DLLs associated with it share approximately 67% of their code with known Petya variants. Bad Rabbit has the potential to spread fast, but […]
Trojan horses are the most dangerous online threats of 2017

The Trojan horse was the world’s most dangerous online threat during the first eight months of 2017, according to stats from antivirus software maker Avira. Trojan horses alone account for 60% of online threats recorded by Avira, with more than 788 million detections during the first eight months of 2017. Trojan horses are malicious programs […]
Keeping phone at your desk reduces productivity, study finds

if you can’t keep your hands off your smartphone, your work will eventually suffer, a new study has found. “People who saw themselves as dependent on their smartphone reported drop-offs in productivity,” says Christian Montag, a psychology professor at the University of Ulm in Germany. “I see a clear connection.” Montag conducted the study, in […]
Three extremely easy tips to improve your browser security

The default settings for most browsers don’t offer users a high level of security. However, there are some quick and easy ways to make your gateway to the Internet slightly more resilient against attacks and data theft. Here are three to get you started. Activate updates According to the computer technology magazine c’t, activating your browser’s […]
Symptoms, solutions for carpal tunnel syndrome

Carpal tunnel syndrome is a condition that creates numbness and tingling in your palm from the thumb to ring fingers. It occurs when a nerve on the palm side of the hand is compressed or irritated in some way. Often, a combination of risk factors contributes to the development of the condition, which tends to […]
Why SSL? The Purpose of using SSL Certificates

SSL is the backbone of our secure Internet and it protects your sensitive information as it travels across the world’s computer networks. SSL is essential for protecting your website, even if it doesn’t handle sensitive information like credit cards. It provides privacy, critical security and data integrity for both your websites and your users’ personal […]
Microsoft’s Hotmail, Outlook.com services back up after outage

Microsoft Corp said its free email services Outlook.com and Hotmail, which suffered an outage across Europe on Monday, were back up. “Everything is up and running,” Microsoft said in a blog post on its Office 365 security site. The outage began at 0720 GMT and continued to affect users across the region for more than […]
USB connections make snooping easy

USB connections, the most common interface used globally to connect external devices to computers, are vulnerable to information ‘leakage’, making them even less secure than has been thought, Australian research has shown. University of Adelaide researchers tested more than 50 different computers and external USB hubs and found that over 90% of them leaked information […]
Are you stuck in a browser rut? Try these six alternatives

People with Windows computers usually use Internet Explorer or Edge, while Mac owners tend to use Safari. But there are plenty of alternatives to Microsoft and Apple’s browsers. Some offer better privacy, others chic design and the ability to personalise. Here’s a look at six of them. Chrome Google’s browser has overtaken Mozilla’s Firefox and […]
ESET reports Birthday Reminder malware

Even trying to remember someone’s birthday can pose a risk, as cyber attackers are not above abusing a simple, popular and harmless-looking app called Birthday Reminder to infiltrate devices. Security company ESET found the adware DNSBirthday distributed around the globe with spikes in the US, Spain, Japan and Italy. The infected Birthday Reminder works properly […]
Business email compromise: Don’t catch that phish!

Business email compromise (also known as “CEO fraud” or the “man in the middle” scheme) is an attack that tricks an individual into transferring money to a criminal’s bank account in response to an email that seems legitimate to the recipient. This scheme affects consumers, business and government agencies — any entity that transfers money online. […]
Managing Passwords

According to the traditional advice — which is still good — a strong password is: Has 12 Characters, Minimum: You need to choose a password that’s long enough. There’s no minimum password length everyone agrees on, but you should generally go for passwords that are a minimum of 12 to 14 characters in length. A […]
Is Ransomware Affecting You?
Learn how iCompuCARE can protect you from ranswomware We have helped many customer protect their systems from getting infected and even restoring infectiosn if it happens
Launching Online Forms
Our Customer can now fill in all request online. This is to enable easier interaction instead of using paper based forms Please access [button link=”https://www.icompucare.com/forms/” type=”big” newwindow=”yes”] iCompuCARE Forms Online[/button]
Online Server Backup to Cloud

iCompuCARE has launched its on Server Backup to cloud. Backup your applications and Accounting Software Automatically into Cloud Secure Offsite Cloud Backup Subscription Add-on for Reliable Data Protection and Cold Disaster Recovery.Simple and reliable cloud integrated backup as a service Unified solution to protect data on-premises and in the cloud 99.9% availability guaranteed Reliable offsite […]
